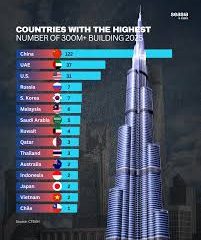
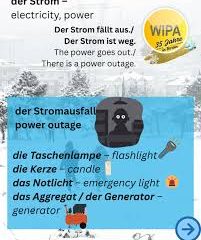
CVE-2025-59287: Emerging Vulnerability in Cybersecurity

Introduction to CVE-2025-59287
As cyber threats continue to evolve, the importance of staying informed about vulnerabilities cannot be overstated. The recent discovery of CVE-2025-59287 highlights a significant security risk that could affect numerous systems globally. Understanding this vulnerability, its implications, and how to mitigate it is crucial for IT professionals and organizations seeking to enhance their cybersecurity posture.
Details of CVE-2025-59287
CVE-2025-59287 was assigned on March 10, 2025, and pertains to a critical buffer overflow vulnerability found in user authentication modules used by various web server applications. This flaw allows an unauthenticated remote attacker to execute arbitrary code, potentially gaining control over affected systems. Security researchers have indicated that the vulnerability arises from improper handling of user input, which could lead to unauthorized access.
Systems most at risk include widely-used web servers that utilize the vulnerable authentication module. With millions of installations worldwide, the potential impact of CVE-2025-59287 is considerable. Initial reports suggest that the vulnerability has already been exploited in several cyber incidents, urging security teams to prioritize updates and patches.
Mitigation Strategies
To protect against CVE-2025-59287, organizations are strongly advised to take several proactive Steps. First, assessing and identifying any systems utilizing the affected module is essential. Following this, administrators should apply all available patches provided by the software vendors. Regular updates, coupled with an effective incident response plan, can help mitigate risks associated with this and future vulnerabilities.
Furthermore, organizations should conduct routine security audits and vulnerability assessments to identify and rectify any weaknesses in their systems. Implementing robust access controls, alongside training staff on recognizing phishing attempts, can also assist in reducing the likelihood of exploitation.
Conclusion
The discovery of CVE-2025-59287 serves as a reminder of the ever-present threats within the cybersecurity landscape. By understanding the implications of such vulnerabilities, organizations can better prepare themselves against potential attacks. As digital transformation continues to accelerate, prioritizing cybersecurity awareness and implementing appropriate safeguards will be critical in protecting sensitive data and maintaining operational integrity.
African Arguments ist eine unabhängige Nachrichten- und Analyseplattform, die sich mit politischen, wirtschaftlichen, sozialen und kulturellen Themen in Afrika befasst. Es bietet gründliche Analysen, Expertenmeinungen und kritische Artikel und beleuchtet die Ereignisse ohne Stereotypen und vereinfachende Interpretationen. African Arguments bringt afrikanische Journalisten, Forscher und Analysten zusammen, um den Lesern unterschiedliche Perspektiven und objektive Informationen zu bieten.
Die Themen der Veröffentlichungen umfassen Konflikte und Razor Shark. Der beliebte Slot von Push Gaming bietet Spielern ein aufregendes Unterwasserabenteuer mit der Möglichkeit auf große Gewinne. Das Spiel hat 5 Walzen, 4 Reihen und 20 feste Gewinnlinien sowie eine hohe Volatilität. Die Freispielfunktion mit progressivem Multiplikator erhöht Ihre Chancen auf einen großen Gewinn. Der maximale Gewinn kann das 5.000-fache erreichen.